One of the things I'm working on at work right now is updating all our iDRACs after Meltdown/Spectre. We had never had the SSL set up, we had just always clicked through the security warning. I got tired of this and decided to setup proper SSL from our enterprise CA,
At first I went to do a manual signing for a multi-year period with a wildcard issued from my enterprise CA, but I decided that automating it with PowerShell would be better, since it would be more dynamic, and scale to more servers.
In this post, I will be talking about setting
- generating a Certificate Signing Request (CSR) from the iDRAC,
- sign it with an enterprise CA,
- uploads the signed cert to the iDRAC, and
- reloads the iDRAC to apply the new cert
To interface with the iDRAC from the script, I'm using Dell Remote Access Controller Administration (RACADM) CLI, which supports remote access.
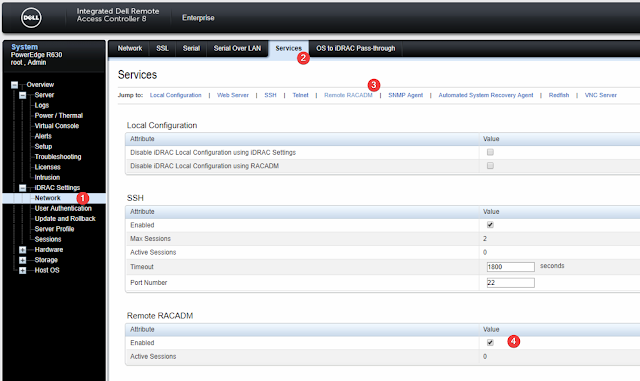
First, you will want to make sure that your iDRAC has Remote RACADM enabled in make sure it is enabled under Network, Services, Remote RACADM in the iDRAC Web UI.
Next, we're going to want to run a few test commands with racadm in a fresh powershell prompt and run
& racadm.exe -r 192.168.100.215 -u root -p calvin getsvctagThis will complain if the SSL certificate is invalid, which is kind of the point of why we are updating it in the first place. So you will probably see output like below
That first line after the certificate warning, is the service tag. I am using -r IP but -r DNS.Host.Name is equally valid, if there is an entry set up, which I would highly recommend.
The script is divided into a few sections
- The Requirements Region - to make sure that we're running with a current version of PowerShell, that we have racadm.exe, and that we have certreq.exe
- Settings to connect to the iDRAC - the IP/hostname, and the credentials to connect to it
- CSR Fields
- Applying DNS and CSR settings to iDRAC
- Generating CSR
- Signing CSR
- Uploading signed certificate to iDRAC and reloading to apply
At first, I was applying the settings with 8+ separate racadm calls, but this was quite time consuming to wait for each to finish. Instead I switched to building a config file and applying that for all the CSR settings at once.
You can pull a cfg or config file of what settings an iDRAC has with
& racadm.exe -r 192.168.100.215 -u root -p calvin get -f $ENV:Temp\file.cfgand there are some interesting line-endings.
This line ending pattern is interesting, but in my testing it was a red-herring and it was perfectly happy if I just made my config file with CR-LF Line endings.
However, I did find that I needed to have my config file I created ANSI encoded. I did this by specifying -Encoding ASCII when I wrote my string with Out-File.



Thanks for this guide, great work.
ReplyDeleteHow can I do multiple servers from the script?
Thanks!
Another thing; getting this error;
ReplyDeleteERROR: The Common Name (CN) field of the CSR Security group must
be configured before a CSR can be generated.
IS this script compatible with v6 of IDRAC?
Thanks
This script saved me a lot of time!!!! Very easy to read. Thank you. Wasn't hard to automate about 100 certs from a CSV.
ReplyDeleteBummer, as of iDRAC Version 4.40, this no longer works, as the "racadm.exe -r $IP -u $idracuser -p $idracpass set -f "$env:temp\$idracName.cfg" function was removed.
ReplyDeleteI had to convert the $idracoptions = @" section to match the XML and then upload the cfg as a xml file to get it to work on the newer version.
I know this a few years old, but do you happen to have a sample of your script?
Delete